The EU Digital Operational Resilience Act (Regulation (EU) 2022/2554, DORA)[1] is a significant legislative step forward, having been in effect for nearly a year with an implementation period stretching until January 17, 2025. Its primary goal is to bolster IT security and resilience in the European financial sector, including the insurance industry. This is achieved through establishing uniform requirements targeting the operational stability and security of information and communication technology (ICT) systems. The comprehensive nature of these new requirements has necessitated many financial companies to overhaul existing processes or adopt new systems, particularly for monitoring third-party ICT providers.
European supervisory authorities, namely the European Securities and Markets Authority (ESMA), the European Banking Authority (EBA), and the European Insurance and Occupational Pensions Authority (EIOPA),[2] are in the process of developing regulatory technical standards (RTS), implementation standards (ITS), and guidelines to provide more detailed specifications for DORA.[3] These documents are currently in draft form and are anticipated to be finalized throughout 2024.
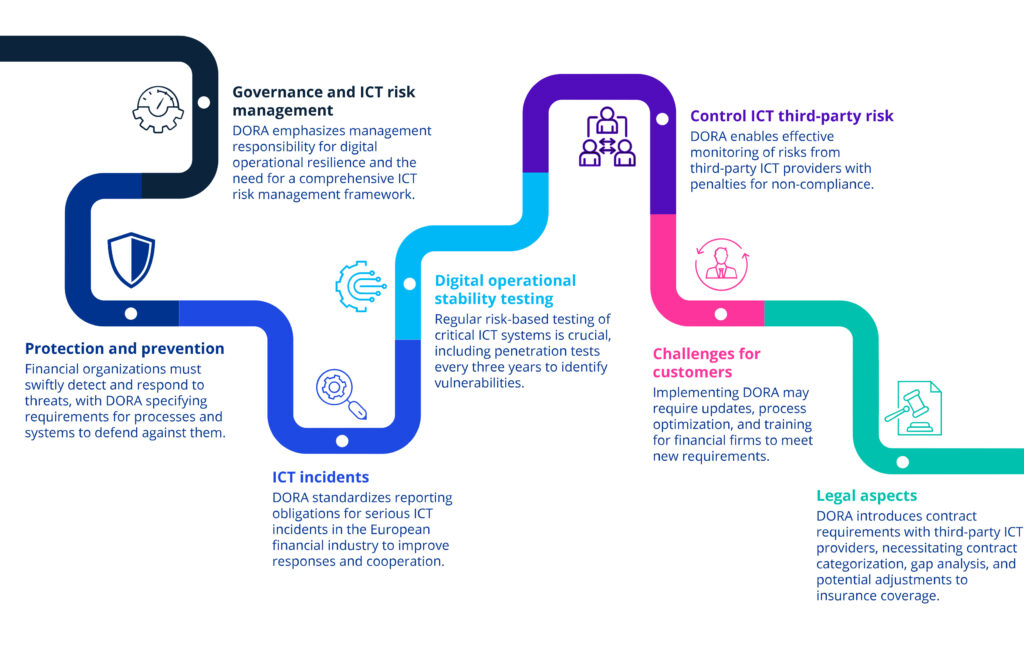
Image: Key areas of the Digital Operational Resilience Act – Source: KPMG, 2023[4]
DORA ICT Risk Management Essentials
Under the new mandates of the EU Digital Operational Resilience Act, companies are required to establish a robust ICT risk management framework. This framework necessitates comprehensive documentation, annual reviews, and continuous improvement strategies. It is particularly vital following significant ICT-related incidents or regulatory findings. Central to this framework is the protection of all information and ICT assets, including pertinent physical components like rooms and data centers. The framework should delineate potential IT risks and the respective risk management strategies, with the ultimate responsibility for implementation resting on the management body of each company.
Additionally, companies must develop further guidelines related to the ICT risk management framework. These entail comprehensive strategies for information security, ensuring the availability, authenticity, integrity, and confidentiality of data and information, and ICT assets. Guidelines will also cover access rights, ICT change management, data backup protocols, and processes for applying patches and updates. A crucial element of these guidelines is the ICT business continuity policy, incorporating business impact analysis and ICT response and recovery plans to guarantee the continuity of critical functions in the wake of an ICT incident.
An internal strategy for digital operational resilience is also mandated. This strategy must outline the implementation of ICT risk management, including risk tolerance thresholds, specific objectives for information security, and mechanisms for detecting ICT-related incidents. Companies are required to maintain a visual network plan and establish a structured approach for network and infrastructure management, prioritizing a risk-based approach.[5]
To ensure that all internal guidelines and strategies are fully operational by the deadline of January 17, 2025, companies are advised to initiate drafting processes immediately. This encompasses establishing internal processes for the continuous identification of all ICT risks, assessing cyber threats, ICT vulnerabilities, and setting up mechanisms with alert thresholds for ICT-related incidents.
Moreover, companies must undertake measures like training employees in ICT security and digital operational resilience, identifying and classifying ICT systems, encrypting data across all states, and managing the lifecycle of cryptographic keys.[6]
Digital Operational Resilience Testing Requirements
Article 25 of the EU Digital Operational Resilience Act (DORA) mandates that all financial companies undertake regular testing for digital operational resilience. This encompasses thorough reviews of ICT business continuity plans, especially those relating to critical or important functions outsourced to third-party ICT service providers. To effectively meet these requirements, financial companies should immediately set in motion a corresponding testing program. This program must specify the frequency of tests, scenarios to be considered, and establish fundamental requirements for test protocols, such as assessing vulnerabilities or network security. The execution of these tests is to be carried out by independent internal or external auditors, ensuring objectivity and reliability.
Additionally, certain financial companies must undertake advanced testing in the form of threat-led penetration testing (TLPT).[7] This directive applies to companies identified by supervisory authorities based on various criteria, including the impact of their services on the financial sector, their significance for financial stability, specific ICT risk profile, ICT maturity level, and other relevant technological characteristics. The specifics of these criteria are to be detailed in a regulatory technical standard (RTS), the public consultation for which commenced in December 2023.[8]
The TLPT involves emulating the tactics, techniques, and procedures of real attackers to conduct controlled and customized live tests. This approach is aimed at providing a realistic assessment of a company’s digital operational resilience, identifying potential vulnerabilities, and ensuring that financial companies are prepared to mitigate and respond to various cyber threats effectively.
Evolving Strategies in ICT Resilience Testing
In an era increasingly dominated by digital operations, regular testing for digital operational resilience is not just a regulatory requirement but a strategic imperative. The financial sector, given its critical role in the economy and its reliance on technology, is particularly focused on enhancing these resilience strategies. The move towards more sophisticated testing methods like TLPT is indicative of the industry’s recognition of the complex and evolving nature of cyber threats. As the technology landscape continues to shift, so too do the strategies for ensuring digital resilience, reflecting an industry that is becoming more proactive and innovative in its approach to risk management and security.[9] The anticipation of these developments and compliance with DORA is a significant step toward safeguarding the stability and integrity of the financial sector.
Managing ICT Third-Party Risk
The EU Digital Operational Resilience Act (DORA) emphasizes the importance of managing ICT third-party risk for financial companies. This risk pertains to the potential vulnerabilities and threats that may arise from the use of ICT services from third-party providers or their subcontractors. In line with this, financial companies are required to develop a comprehensive strategy to address third-party ICT risk. This includes conducting a pre-contractual risk analysis to ensure that third-party ICT service providers adhere to appropriate information security standards, especially when such services are critical or important to the company’s operations.
For services deemed critical or important, financial companies must verify that third-party ICT providers are employing the latest and most robust information security standards. Additionally, companies must annually report the type and number of new ICT contracts to BaFin and adhere to the minimum contract contents outlined in Article 30 of DORA. To streamline this process, companies are encouraged to have standardized contract templates that can be tailored as needed for new agreements.
The classification of third-party ICT providers is undertaken by European supervisory authorities based on criteria set forth in Article 31, paragraph 2 of DORA. A critical ICT service provider is identified if its services systematically impact the stability, continuity, or quality of the services of the financial company, among other criteria. Detailed rules regarding this classification will be provided in a delegated regulation of the EU Commission, which is still pending final adoption.
Financial companies are ultimately responsible for the oversight of ICT service providers. This includes ensuring that critical third-party ICT service providers establish a registered office in the EU within 12 months of being classified as critical. While there’s no requirement for data to be stored within the EU, the supervisory authority can suspend or terminate the use of a critical third-party ICT service provider if risks are not adequately managed.
Furthermore, critical third-party ICT service providers fall under the purview of European supervisory authorities, which have the power to request information, conduct inspections, issue recommendations, publish information on non-compliance, and impose fines for violations. However, the scope of these powers is generally more limited compared to those exercised over financial companies.
Recent Focus on Third-Party ICT Providers
In the digital age, financial companies increasingly rely on third-party ICT providers for critical services. With this dependency comes the need for stringent oversight and risk management strategies. The evolving landscape of ICT services, particularly the rise of cloud computing, demands careful selection and monitoring of third-party providers.[10] As the financial sector braces for the finalization and implementation of these regulatory standards, there’s a growing emphasis on the early identification and management of risks associated with third-party ICT services. This trend is reflective of a broader shift towards greater accountability and proactive risk management in the financial industry, underscoring the importance of digital operational resilience in maintaining the stability and integrity of financial services.
Sources
-
https://eur-lex.europa.eu/legal-content/en/TXT/?uri=CELEX:32022R2554 ↑
-
https://www.eiopa.europa.eu/digital-operational-resilience-act-dora_en ↑
-
https://www.eiopa.europa.eu/esas-launch-joint-consultation-second-batch-policy-mandates-under-digital-operational-resilience-act-2023-12-08_en ↑
-
https://kpmg.com/xx/en/home/insights/2023/10/digital-operational-resilience-act.html ↑
-
https://www.ey.com/en_be/financial-services/how-to-prepare-for-the-digital-operational-resilience-act ↑
-
https://www.digital-operational-resilience-act.com/DORA_Training.html ↑
-
https://extranet.eba.europa.eu/sites/default/documents/files/document_library/Publications/Consultations/2024/JC%20DORA/1064201/JC%202023%2072%20-%20CP%20on%20draft%20RTS%20on%20TLPT.pdf?retry=1 ↑
-
https://www.eiopa.europa.eu/consultations/dora-public-consultation-second-batch-policy-products_en ↑
-
https://www.pwc.com/mt/en/publications/technology/dora.html ↑
-
https://www2.deloitte.com/content/dam/Deloitte/no/Documents/risk/Deloitte-DORA.pdf ↑


